Solutions
Performance-based OT security is here.
Wondering why you don’t make progress in OT security? It’s because you are using the wrong tools. OTbase lets you systematically raise your security posture by focusing on what you can actually control, and by integrating disperse security efforts into one platform where everything is connected.
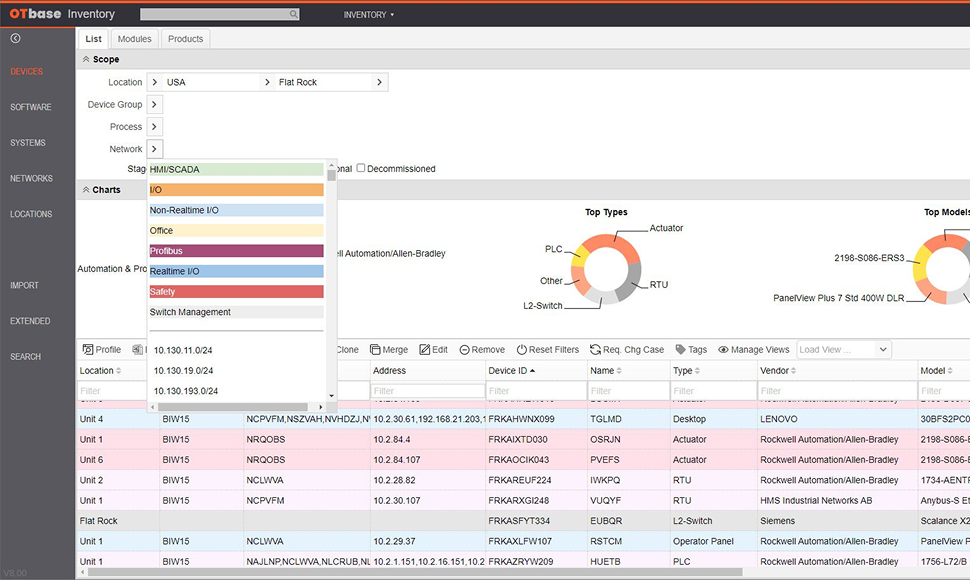
Start with a contextualized OT asset inventory
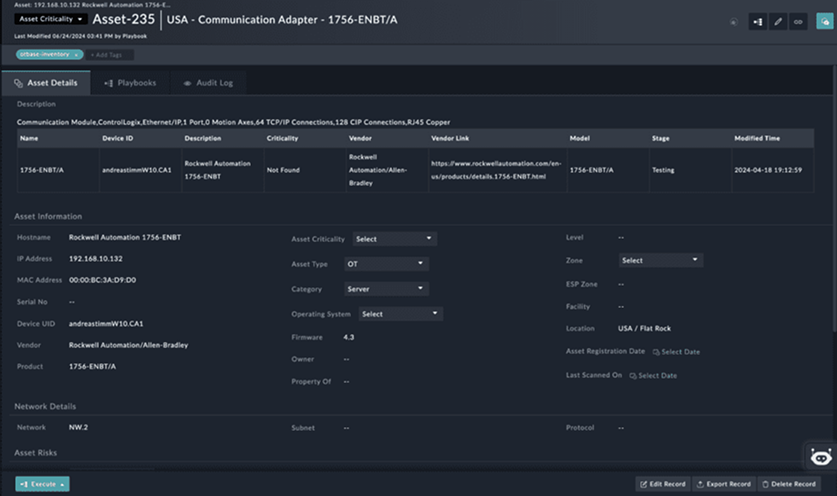
A contextualized OT asset inventory is the first step of every successful OT security journey. Contextualized means that not only you’re able to see exact software and firmware configurations, which are essential for vulnerability mapping, but also process related metadata that allows you to establish criticality and target security levels. OTbase takes your system understanding to a whole new level.
Make your OT vulnerability management effective
Most OT vulnerability management exercises suffer from the fact that they are purely anecdotal. The latest vulnerability is hyped on social media or by government agencies, and your team scrambles to figure out if you are affected. At the same time you ignore your vast vulnerability backlog.
OTbase provides a reliable and detailed account of all known vulnerabilities that affect your installed base. Along with the capability to filter for geolocation, process association, required attack complexity, known exploits, device criticality, the works. You also get the opportunity to create remediation tasks that you can assign to individuals, along with deadlines, suggested remediation, file attachments, and more.
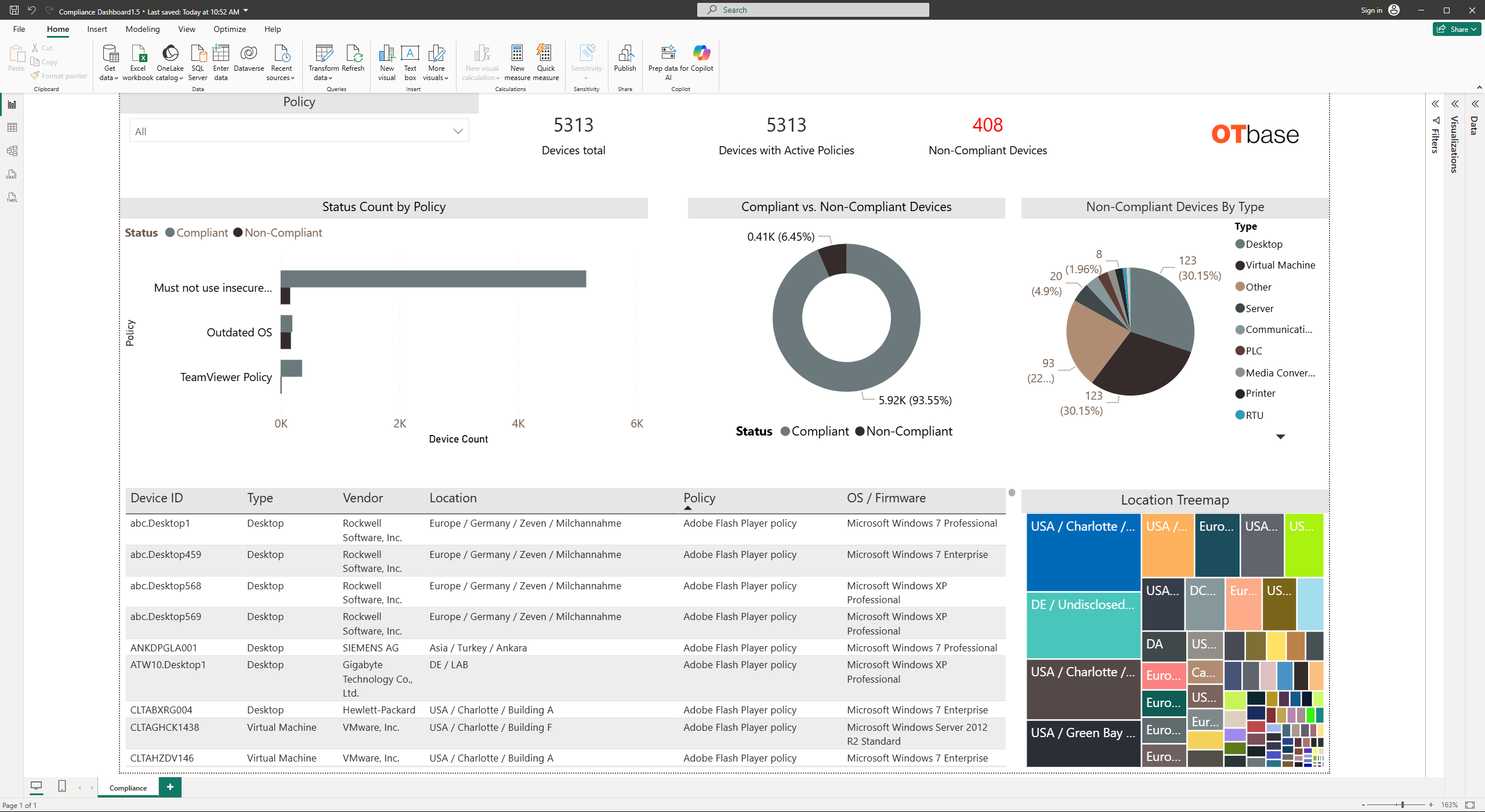
Become proactive with automated configuration policy audits
It’s not all that difficult to figure out which configurations and software products cause the bulk of critical vulnerabilities. By establishing configuration policies, your team moves from reactive to proactive. OTbase allows you to spot compliance and non-compliance by continuous reporting. You don’t even need to send the auditor on site, becaus all the data is available at your fingertips, and up to date.
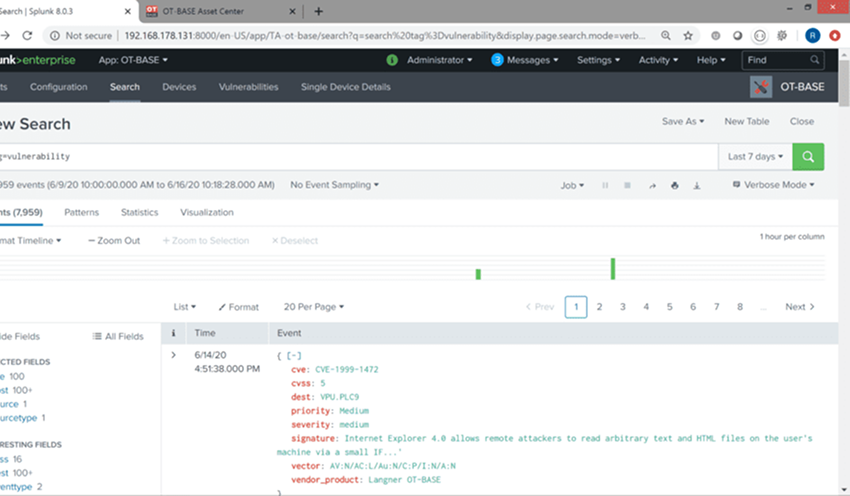
Contextualize SIEM alerts
Have you seen this: Your SIEM platform generates an alert, and the SOC team now has to figure out which device the IP address 192.168.0.4 belongs to. Or a specific MAC address, for that matter. A process that can take many hours, if not days.
If the SIEM is able, however, to contextualize basic address information with the rich asset information in OTbase, it’s a matter of minutes to identify the nature of the associated device, its location, process function, network neighborhood etc.
Standard OTbase integrations are available for Splunk and FortiSOAR.
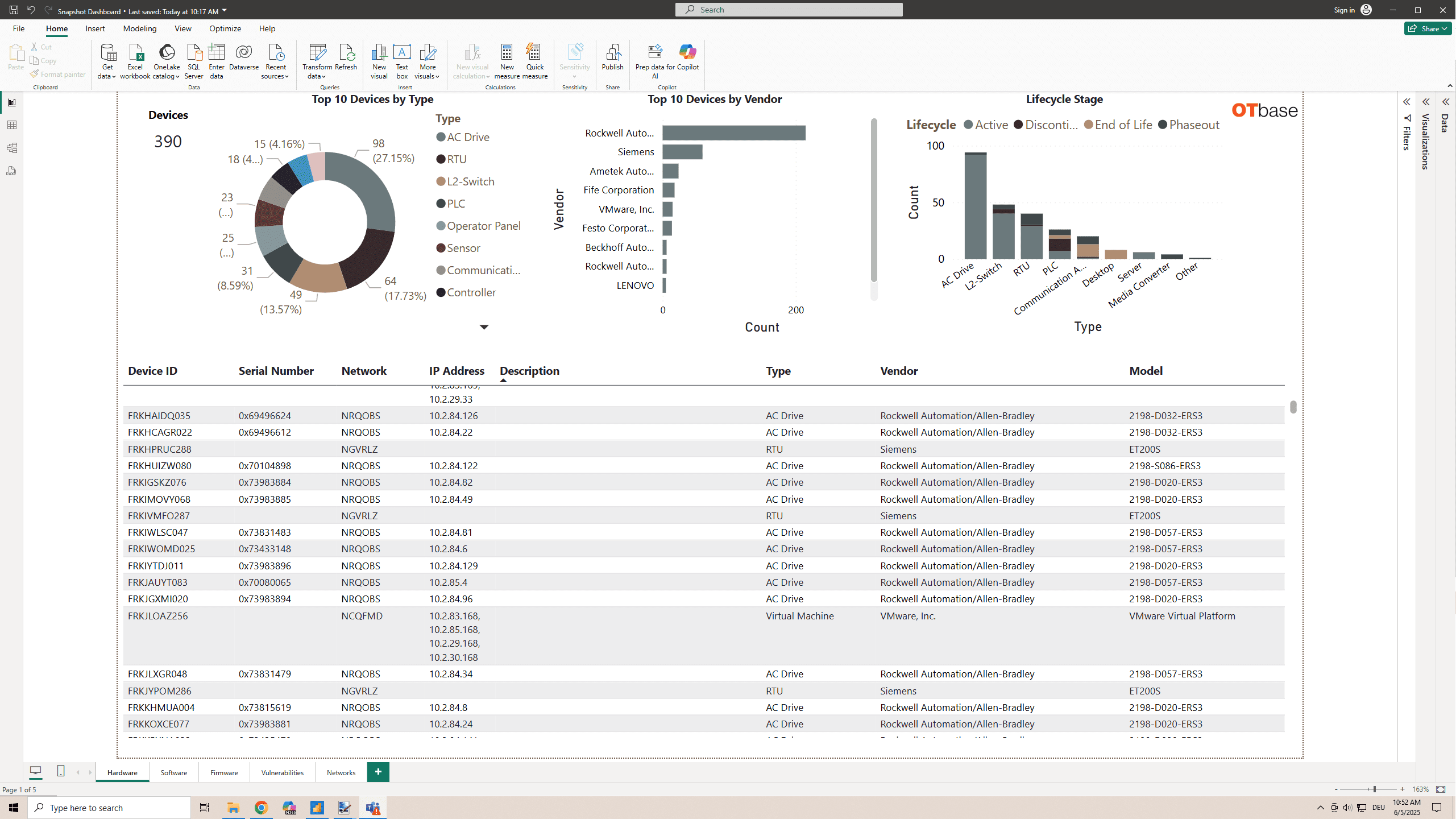
Create awesome reports
OT security is a numbers game, and no progress is to be made if the numbers aren’t collected, reported, and analysed properly. For this reason, OTbase includes a multitude of built-in metrics and reporting options. However, top of the line is the OTbase Connector for Microsoft Power BI, which allows you to generate game-changing dashboards and reports in the tool that the C suite loves.
Want to learn more? Check out the OT vulnerability management handbook
The vast majority of OT asset owners is anything but happy about their progress in reducing the OT attack surface. And it’s getting clear what the primary reason is: If you rely on threat detection products, progress just won’t happen — because threat detection is reactive by nature. Most likely you will also be frustrated by the high number of false-positive alerts.
Progress can only happen outside of the SOC, in the engineering space, where you can achieve actual and measurable reductions of the attack surface. This is the approach taken by OTbase.