Automate your OT Audit
Gone are the days when OT audits involved travel and time-consuming walk-down inspections. Gone as well are nasty surpises from audit results. With OTbase, you always know right away which systems are in compliance with company policies, and which ones aren’t. Welcome to the OTbase Audit Workspace.
The key to
proactive OT security
If all you do is chase vulnerabilities as they drop in, you will be caught in a hamster wheel of pain. OT security policies and audits are a major, and well-proven tool to make OT security efforts proactive.
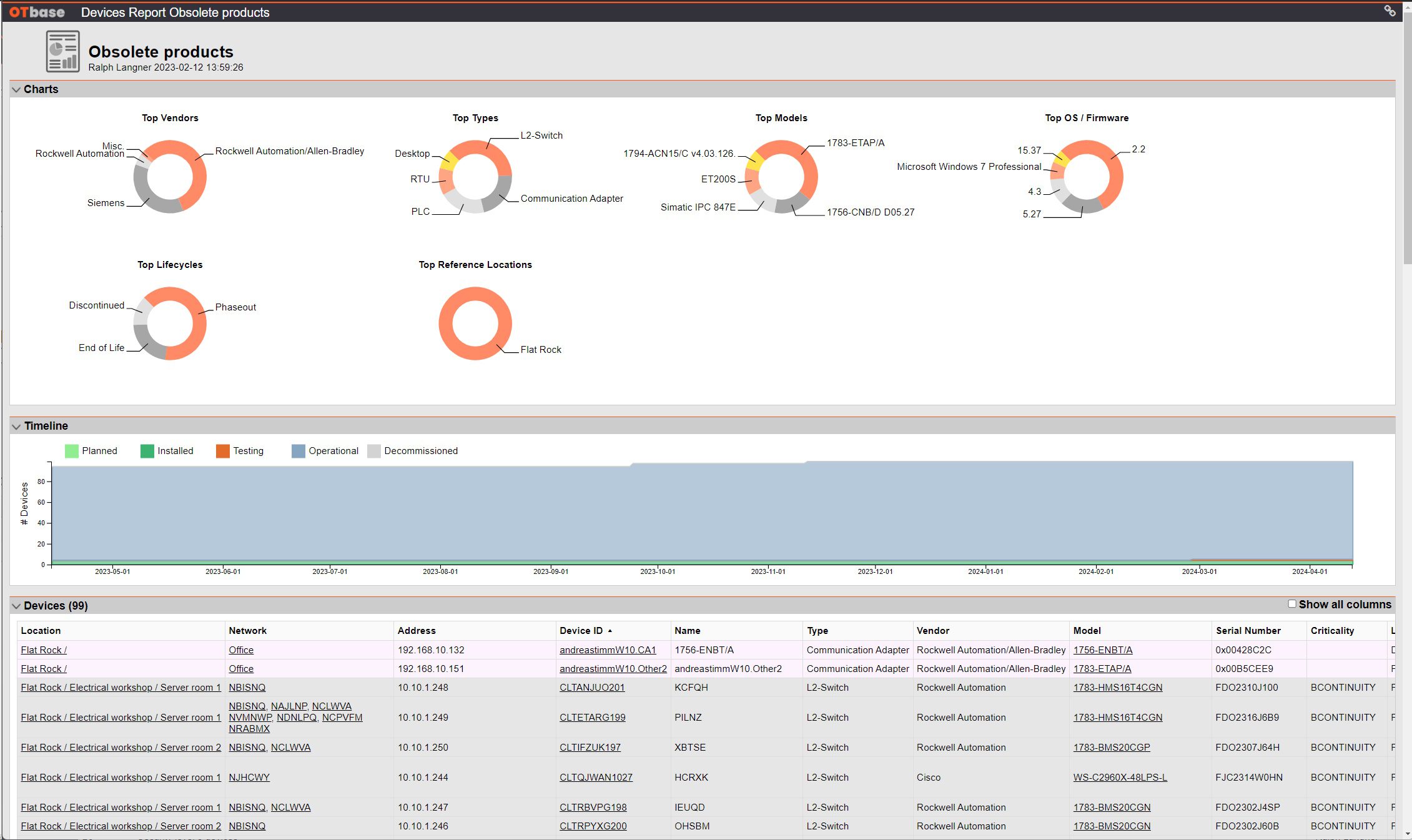
Based on OTbase’s comprehensive OT asset inventory, it becomes easy to identify potential sources of grief: Computers running outdated operating system versions, usage of insecure protocols like Telnet and HTTP, missing or disabled anti-virus software, and so much more.
OTbase will spot all of them instantly and point you and your team to non-compliant configurations in realtime. No walk-down inspections. Instant present-day reports.

Here’s how it’s done:
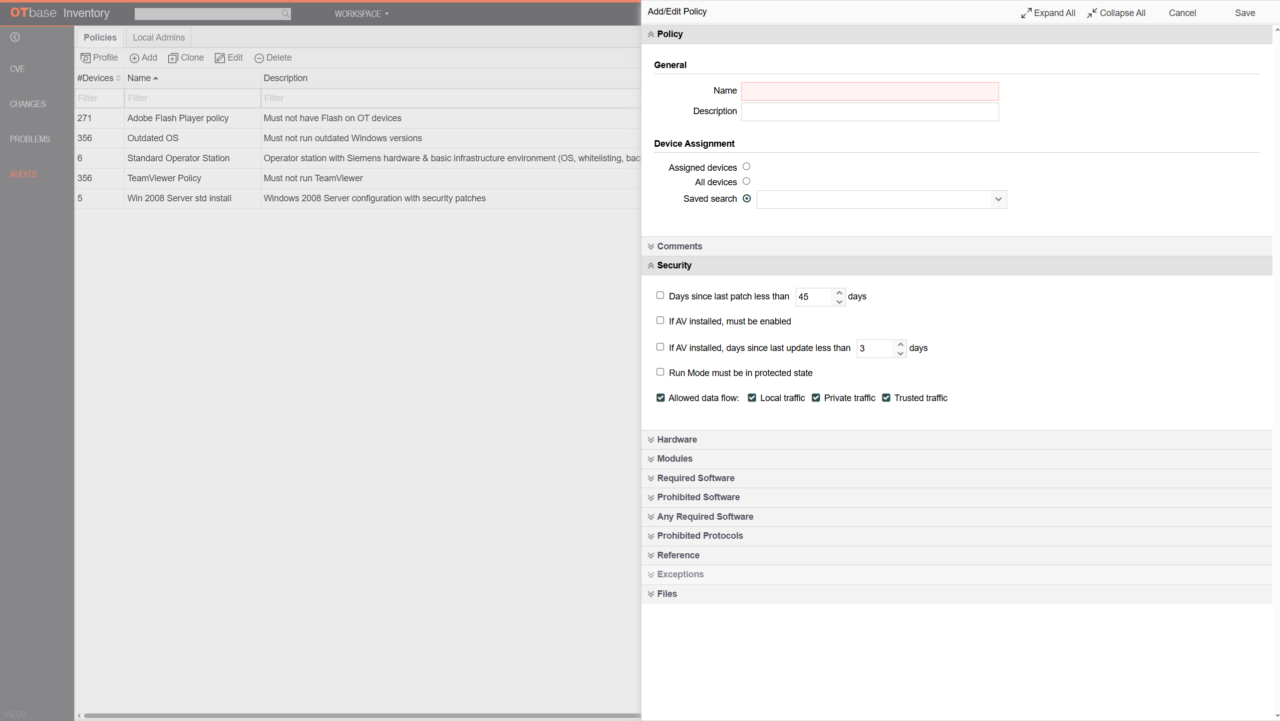
Craft your policies within minutes
The audit workspace in OTbase lets you check for security settings, required or prohibited software, insecure network protocols, and more. You can limit your policies to particular sets of devices, and you can also accommodate policy exceptions for individual devices.
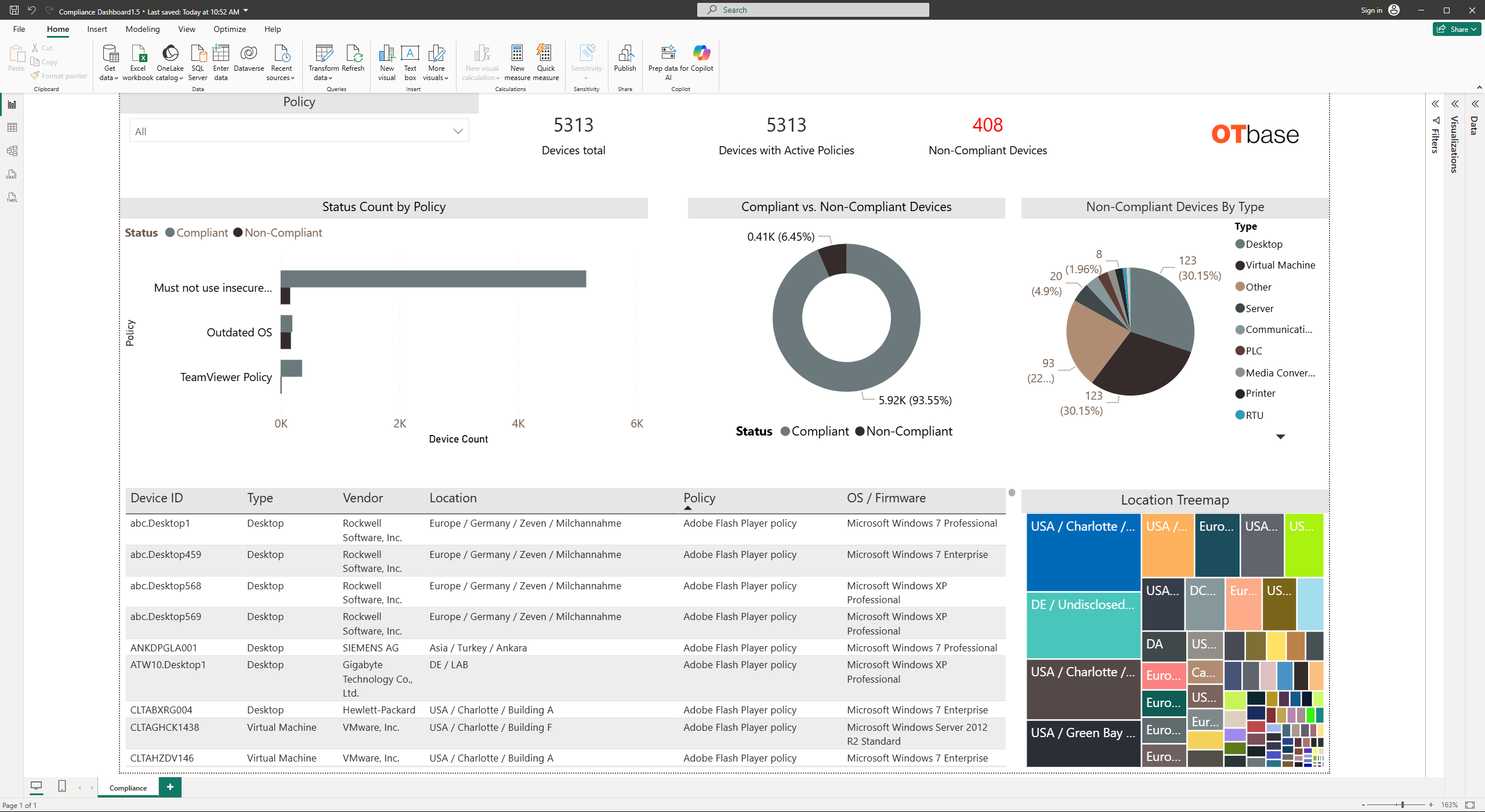
Audit your policies
Once that you have defined your policies, OTbase will automatically create evergreen reports that shows compliance and non-compliance in realtime, along with developments over time. You can see where non-compliant devices are, and drill-down into any particular machine. It doesn’t get any easier.
Take control with manually added device metadata
The OT Asset Inventory Handbook outlines the requirements for an OT asset inventory that’s actually useful. You’ll read about:
- Legacy OT asset inventories
- Getting the must-have data from your devices
- Populating an OT asset inventory
- And managing access controls