OT Security Blog
Insights on Resilience, Vulnerability Management, and More
OT Asset Management in 2024: A product category in its own right
Back in 2017 when we launched the OTbase software product, we were wondering how to label it. The initial idea was to call it an “OT management system”. That seemed…

Transform OT User Access Control: A Deep Dive into OTbase Inventory’s Capabilities
With OTbase Inventory, organizations have a comprehensive tool for managing user access in a nuanced and effective manner. It’s not just about limiting access; it’s about optimizing it for operational efficiency.
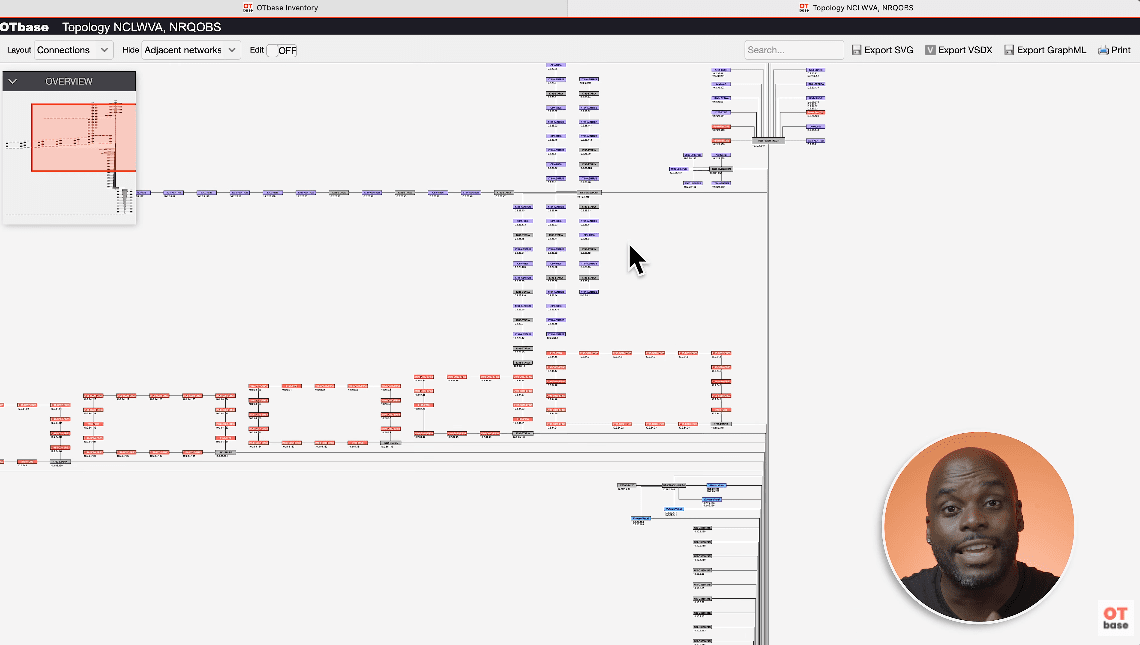
Mastering the Intricacies of OT Network Topology: A Guide to Simplifying Complexity
With tools like OTbase Inventory, the management of network topology in OT has reached a new level of sophistication. It’s not just about visualizing networks; it’s about gaining actionable insights for effective management.
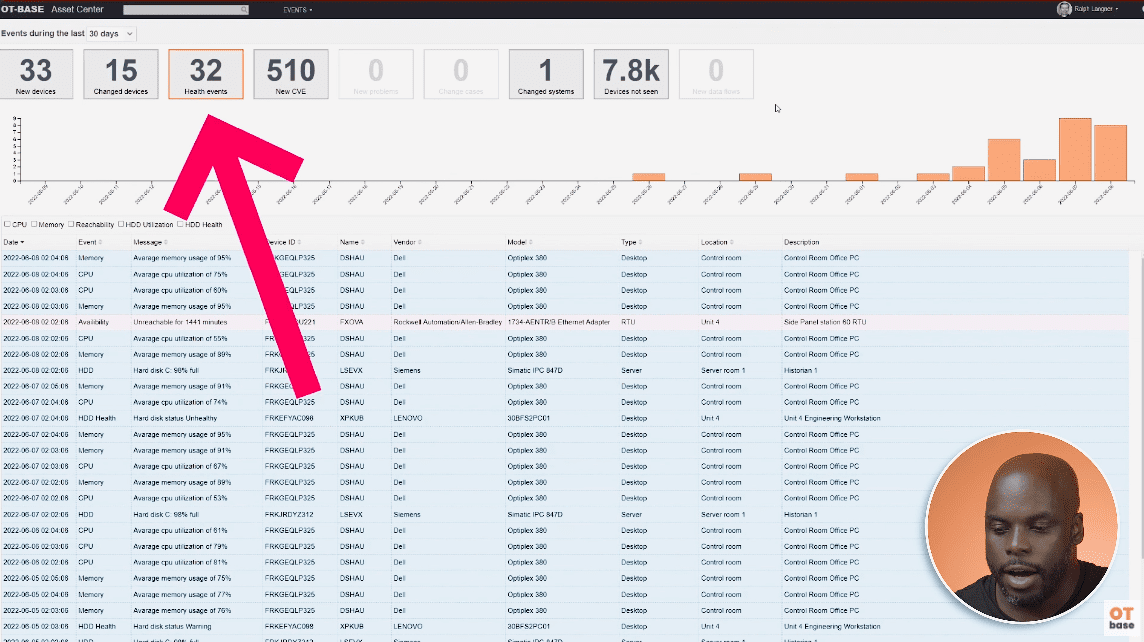
Why tracking OT Asset Health is even more important than network anomaly detection
In the evolving landscape of Operational Technology (OT), asset management has transitioned from being an operational necessity to a strategic advantage.

The OT cyber risk they didn’t tell you about
When you have spent some time in operations technology in the last decade, it is practically impossible that you hadn’t been informed about cyber risk: The risk of falling victim…
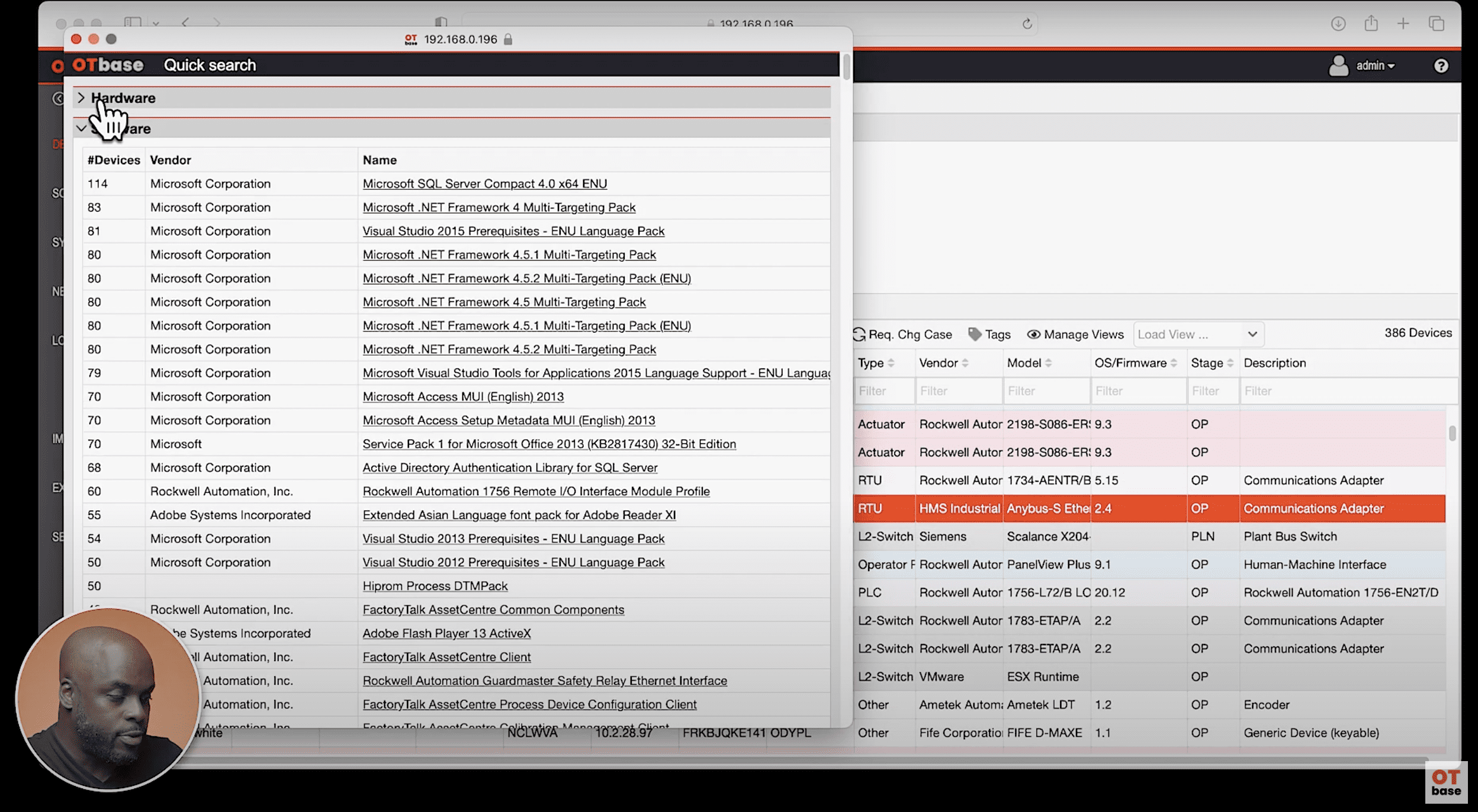
Struggling to Find Your OT Assets? Speed Up Your Search with OTbase Quick Search
In our previous blog post, we explored how OTbase Asset Management Software helps you match CVE data to your devices. Today, we’re diving into another powerful feature of OTbase Asset…
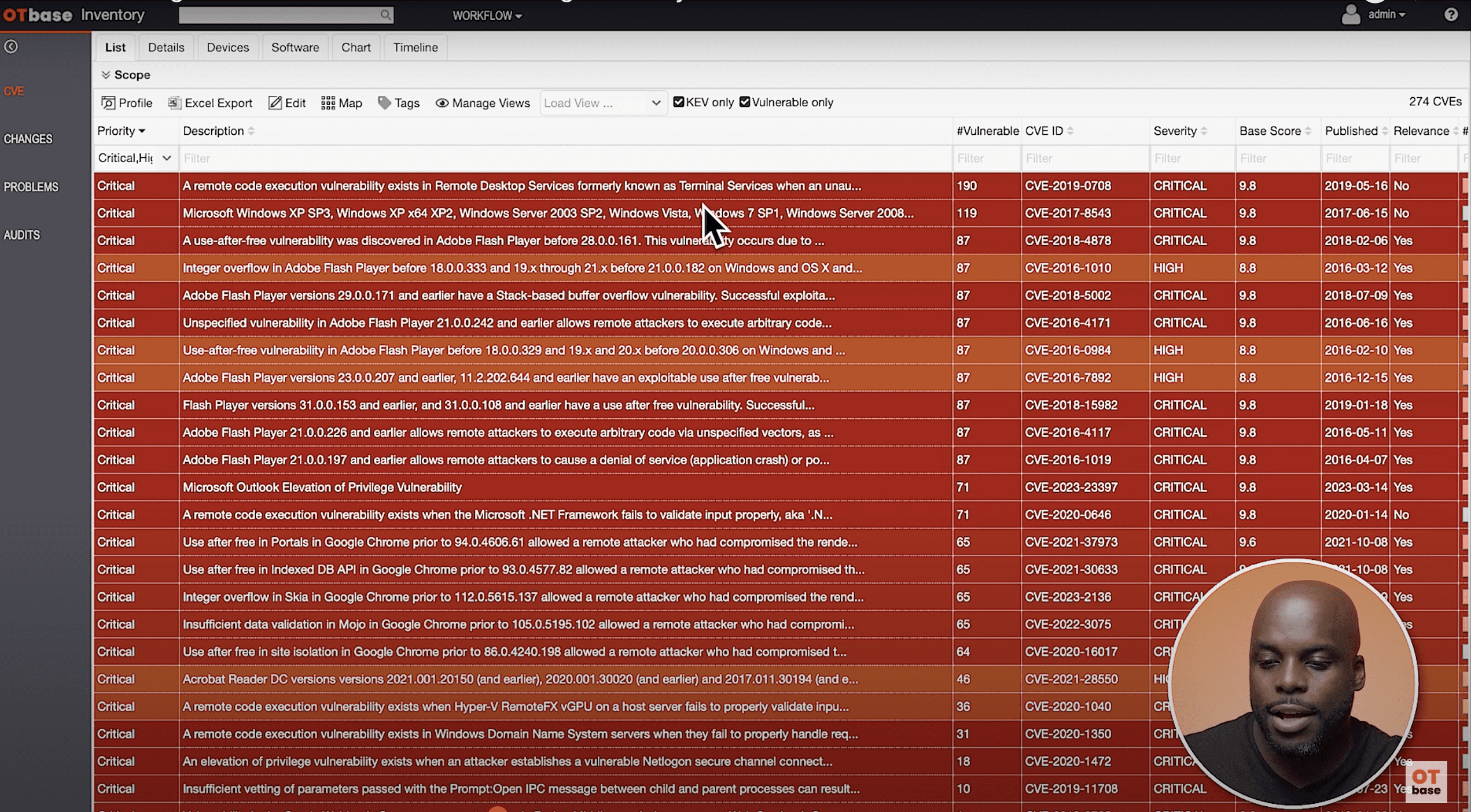
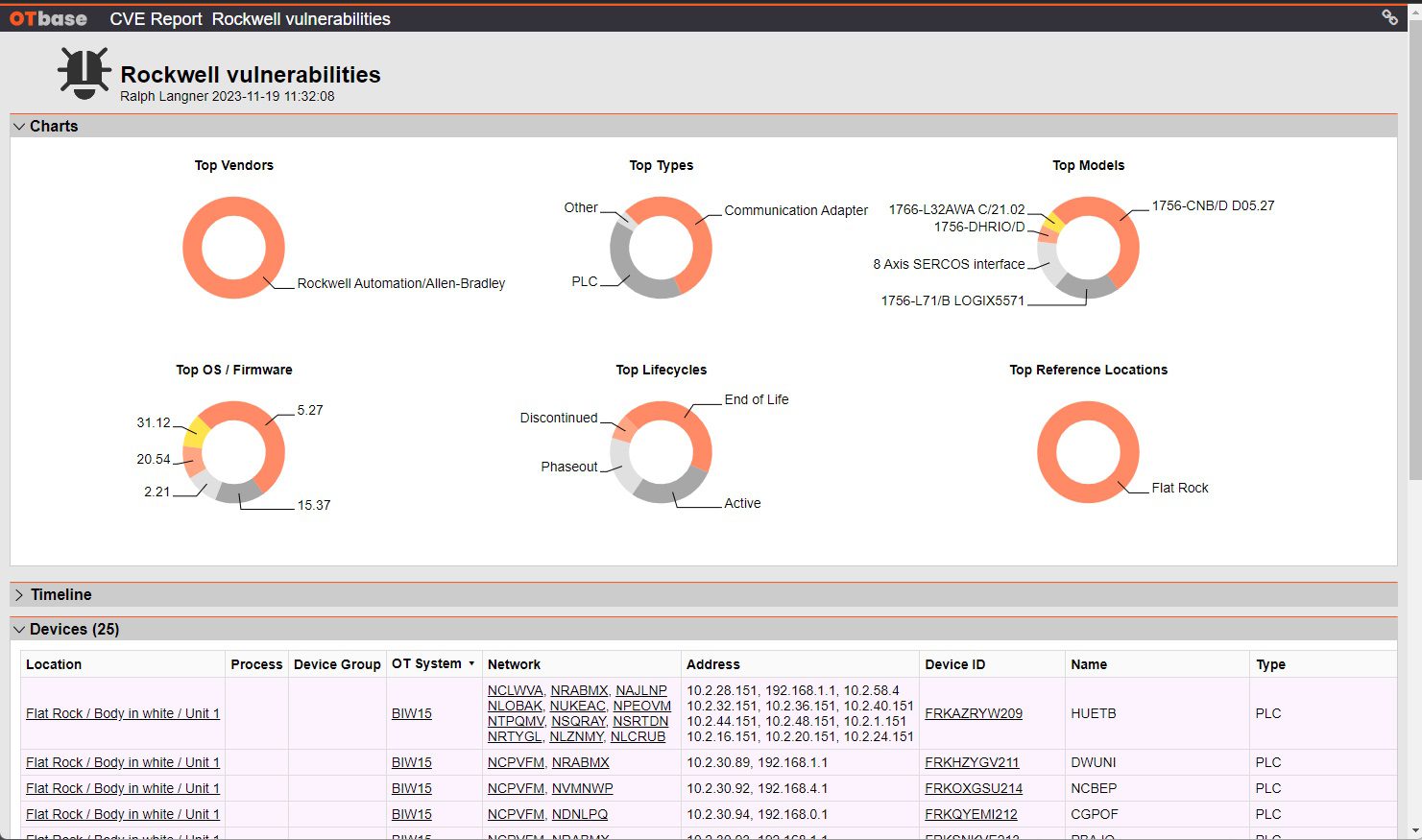
Mastering CVE Matching for OT assets
In the world of Operational Technology (OT), we find several orders of magnitudes more vulnerabilities than in IT. Therefore, vulnerability identification and management becomes a much more challenging task that…

Maintaining OT Resilience: Balancing Security and Engineering Needs
Several other engineering use cases are just as important, if not more so. In this blog post, we’ll explore some of the engineering use cases OTbase addresses and explain why they’re just as crucial as managing common security use cases.
Mastering OT Vulnerability Management: Simplifying the Process with Automation
A single vulnerability can cause substantial damage to critical infrastructure and result in significant security breaches. However, managing OT vulnerabilities is not always a simple process. It can be intimidating, especially when performed manually. Therefore, OT vulnerability management must be automated to increase efficiency and effectiveness.
5 Reasons Why Effective OT Security Requires An Accurate Asset Inventory
In the current digital era, the manufacturing and oil and gas industries extensively rely on technology to increase efficiency and productivity. However, as technological dependence increases, so does the risk of cyber attacks and security breaches. For the success of these industries, an effective operational technology (OT) asset inventory is essential.

Why Passive Scanning Won’t Cut It: Oil and Gas Companies Need Active Probing
Oil and gas companies must use active probing as part of their OT strategy if they want to stay safe, reliable, and efficient. This will give us the visibility, speed, and accuracy we need to find threats and issues quickly, deal with them, and fix them before they become big problems.

What are Tangible Results in OT Security?
Fact is that oftentimes the chances that an asset owner’s investment in ICS Detection technology and related services easily exceeds the damage that could reasonably be expected from a cyber-physical attack.
