OT Security Blog
Insights on Resilience, Vulnerability Management, and More

Boyes: Use common sense in OT security
By Walt Boyes Our last article identified some serious and quantifiable risks for cyberinfrastructure failure not caused by external threat actors. These risks form the basis for most cyber threats…

Boyes: OT security defenders need to look inside, not outside
By Walt Boyes For over a decade, we have been reacting to the fear of cyber intrusion into OT (Operations Technology) networks in our industrial process plants, refineries, pipelines, and…
IT/OT Collaboration: The Blueprint for Operational Synergy
There is a notion that IT and OT teams are like oil and water. The two, even when inhabiting the same space, remain separate. Many companies treat the two teams…

IT/OT Convergence – the foundation of digital transition
In 2025, IT and OT teams in many organizations continue to work independently of one another. But there is a paradigm shift happening. The two, as they have been for…
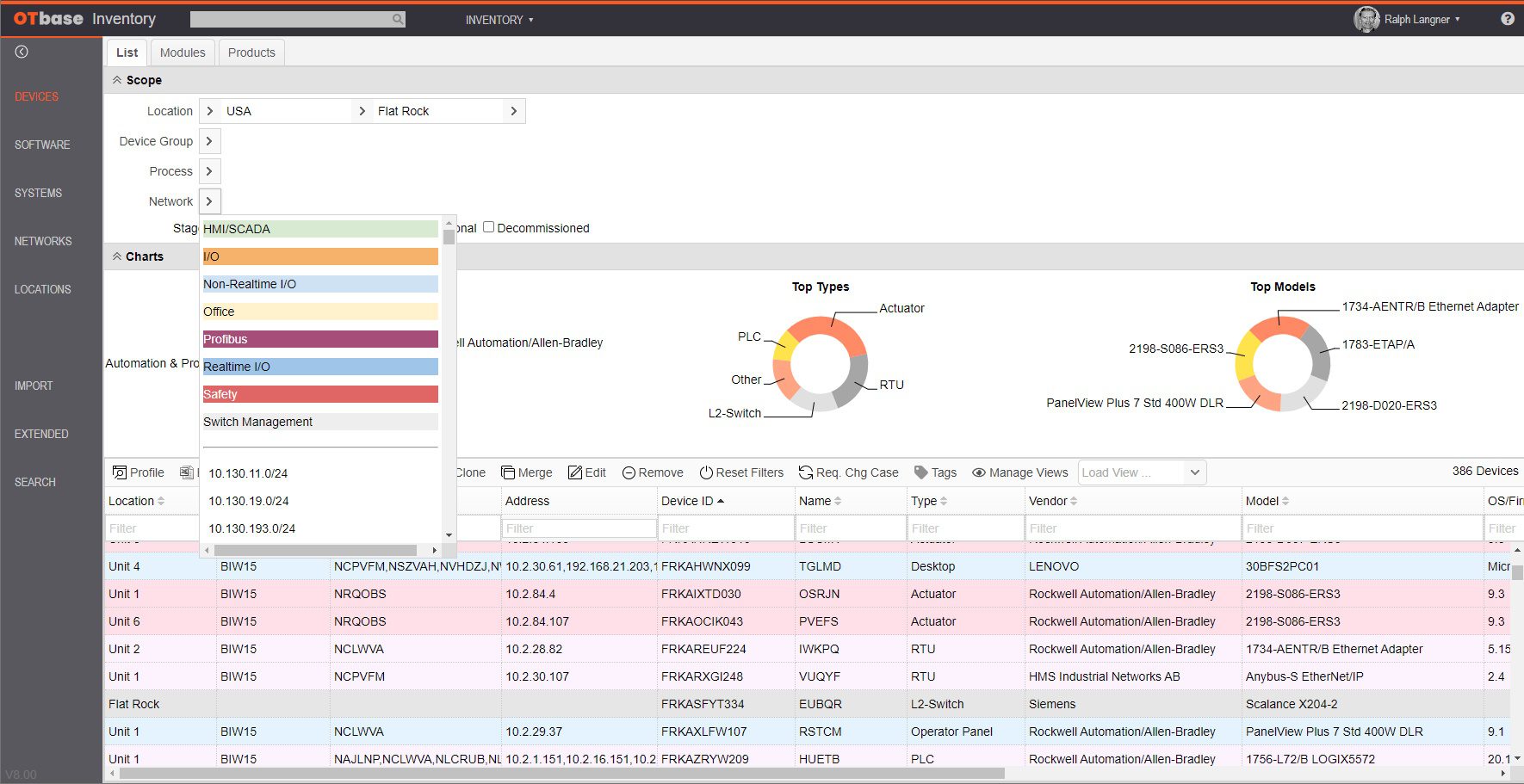
Using Automated Audits for Continuous Improvement in OT Security
Chances are, you have a real problem on your hands. More than likely, at least one Windows machine in your installed base is running Windows XP. You don’t have to…
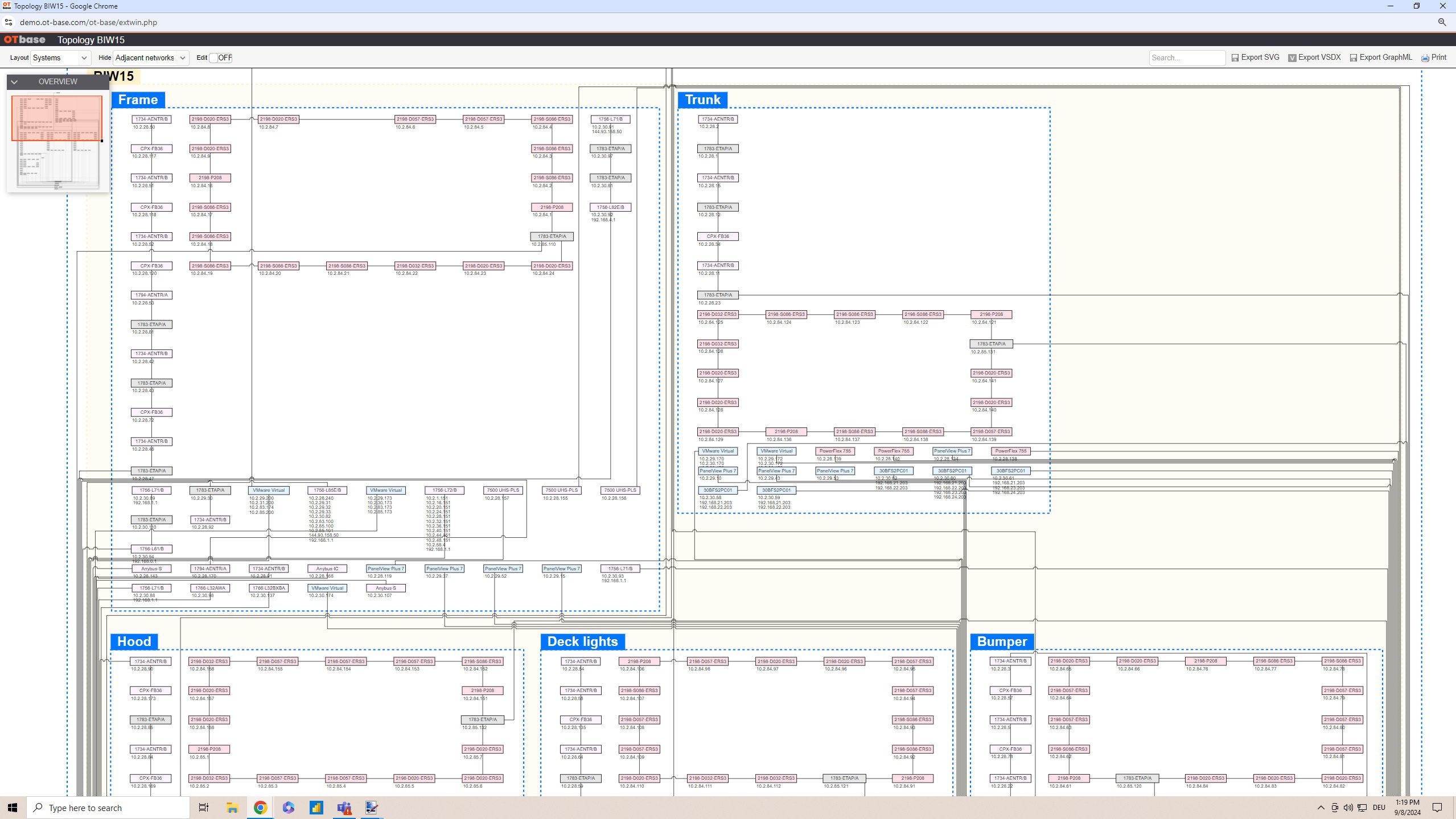
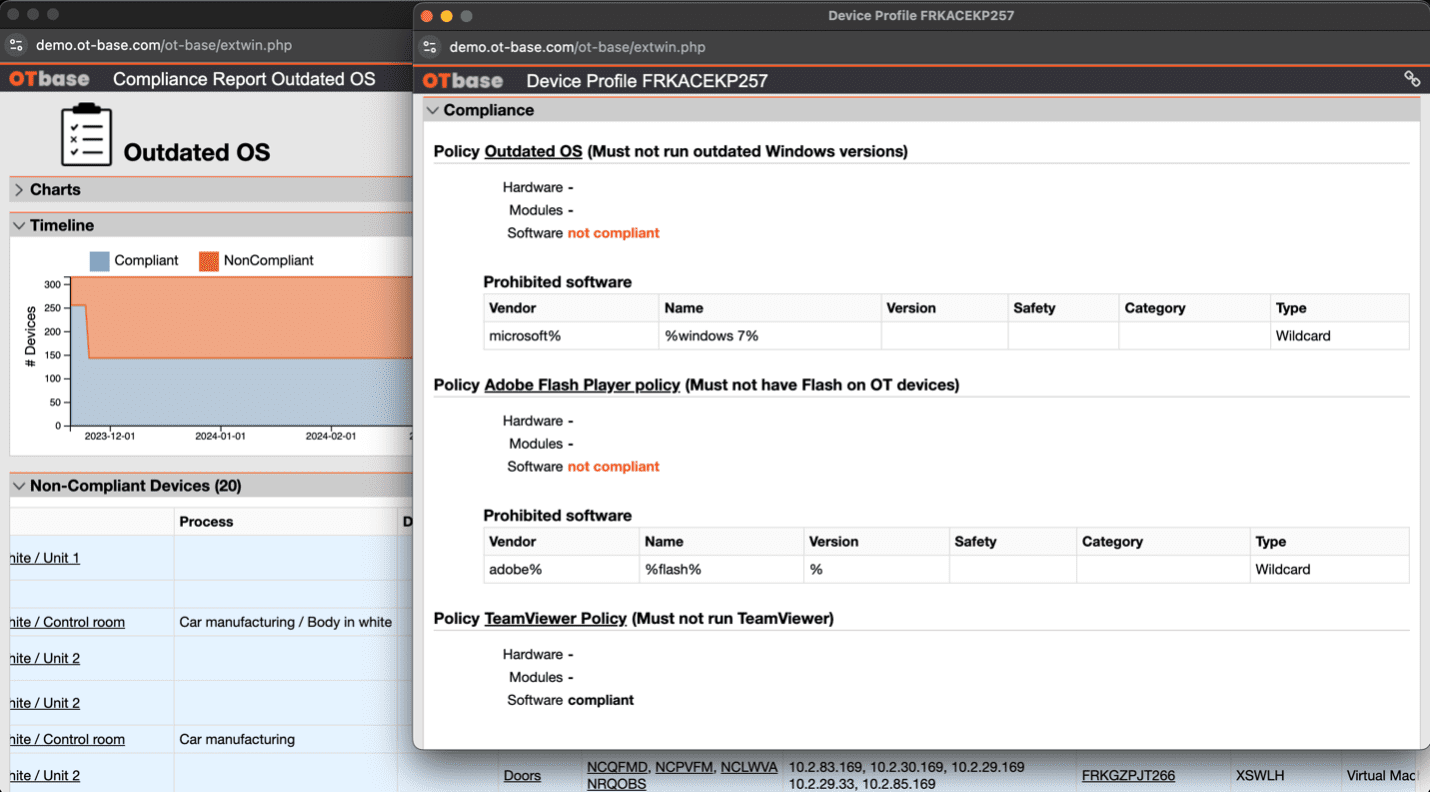
Beyond OT security basics: The role of an OT network inventory
OT environments usually stretch over hundreds of networks – each varying in criticality to whatever industrial processes they’re a part of. But it isn’t easy to converse about OT security…
Effective OT vulnerability management: Prioritizing what matters
Operational Technology (OT) vulnerability management is a critical focus for large enterprises seeking to protect their critical infrastructure. As OT systems increasingly converge with IT networks, managing vulnerabilities effectively is…

Thinking outside of the box: Mastering OT security is not about defending against threats
Fact is that oftentimes the chances that an asset owner’s investment in ICS Detection technology and related services easily exceeds the damage that could reasonably be expected from a cyber-physical attack.

Understanding The Basics of OT asset management
By following these basic principles, organizations can effectively manage their operational technology assets, ensure their reliability and security, and optimize the performance of their industrial processes.
The big OT asset visibility misconception
You have heard it a dozen times: You cannot protect what you don’t see. You need asset visibility! Based on this trivial insight, OT security vendors usually explain how you…
Threat-centric vs. infrastructure-centric OT security
There are two general approaches to OT security. One approach is threat-centric and attempts to identify and eliminate cyber threats in OT networks. The other approach is infrastructure-centric and largely…

Compound OT security gains
Guess what, the biggest problem in OT security isn’t the ever changing threat landscape. It’s the inefficiency of popular OT security strategies and processes. Why inefficient? Simply because they don’t…
