OT Security Blog
Insights on Resilience, Vulnerability Management, and More

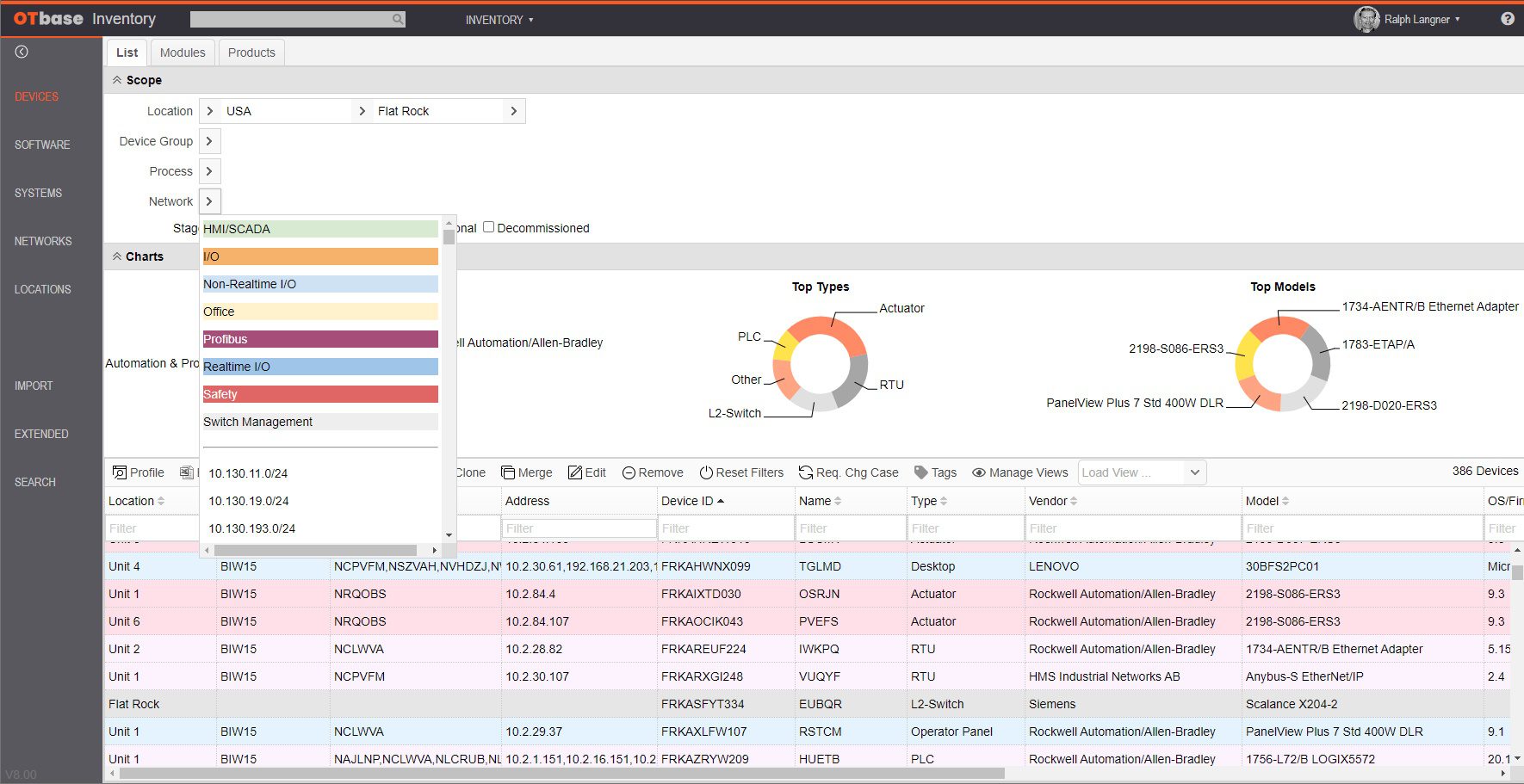
OT asset inventory made easy
By Walt Boyes This is part of a blog series. Please read Part I and Part II here. When last we left our hero, he was juggling maintenance issues and…

Contextual metadata ties technical OT asset information to use cases
By Walt Boyes This is part of a blog series. Please read Part I here. Our hero has been trying his very best to follow rule number one: you cannot…

Why manual OT asset inventories don’t work
By Walt Boyes When we last saw our intrepid maintenance lead cybersecurity chief, he was waking up in the middle of the night from dreams of being the little Dutch…

When Cybersecurity Vendors focus on the OT network and ignore the Plant Floor
By Walt Boyes Congratulations! Along with your other responsibilities as Maintenance Engineer, your boss has just appointed you OT Cybersecurity lead. So now you have to find time and budget…

Boyes: No OT vulnerability management without an OT asset inventory
By Walt Boyes What we know is that we can’t manage OT asset vulnerabilities from the vulnerability side of the equation. We know that doesn’t work, because the vulnerability space…

Boyes: Taking a hard look at OT threat detection
By Walt Boyes When you want to control something, you must measure it. You cannot control something you cannot measure. That’s what we do in OT- we measure and then…

Boyes: Use common sense in OT security
By Walt Boyes Our last article identified some serious and quantifiable risks for cyberinfrastructure failure not caused by external threat actors. These risks form the basis for most cyber threats…

Boyes: OT security defenders need to look inside, not outside
By Walt Boyes For over a decade, we have been reacting to the fear of cyber intrusion into OT (Operations Technology) networks in our industrial process plants, refineries, pipelines, and…
IT/OT Collaboration: The Blueprint for Operational Synergy
There is a notion that IT and OT teams are like oil and water. The two, even when inhabiting the same space, remain separate. Many companies treat the two teams…

IT/OT Convergence – the foundation of digital transition
In 2025, IT and OT teams in many organizations continue to work independently of one another. But there is a paradigm shift happening. The two, as they have been for…
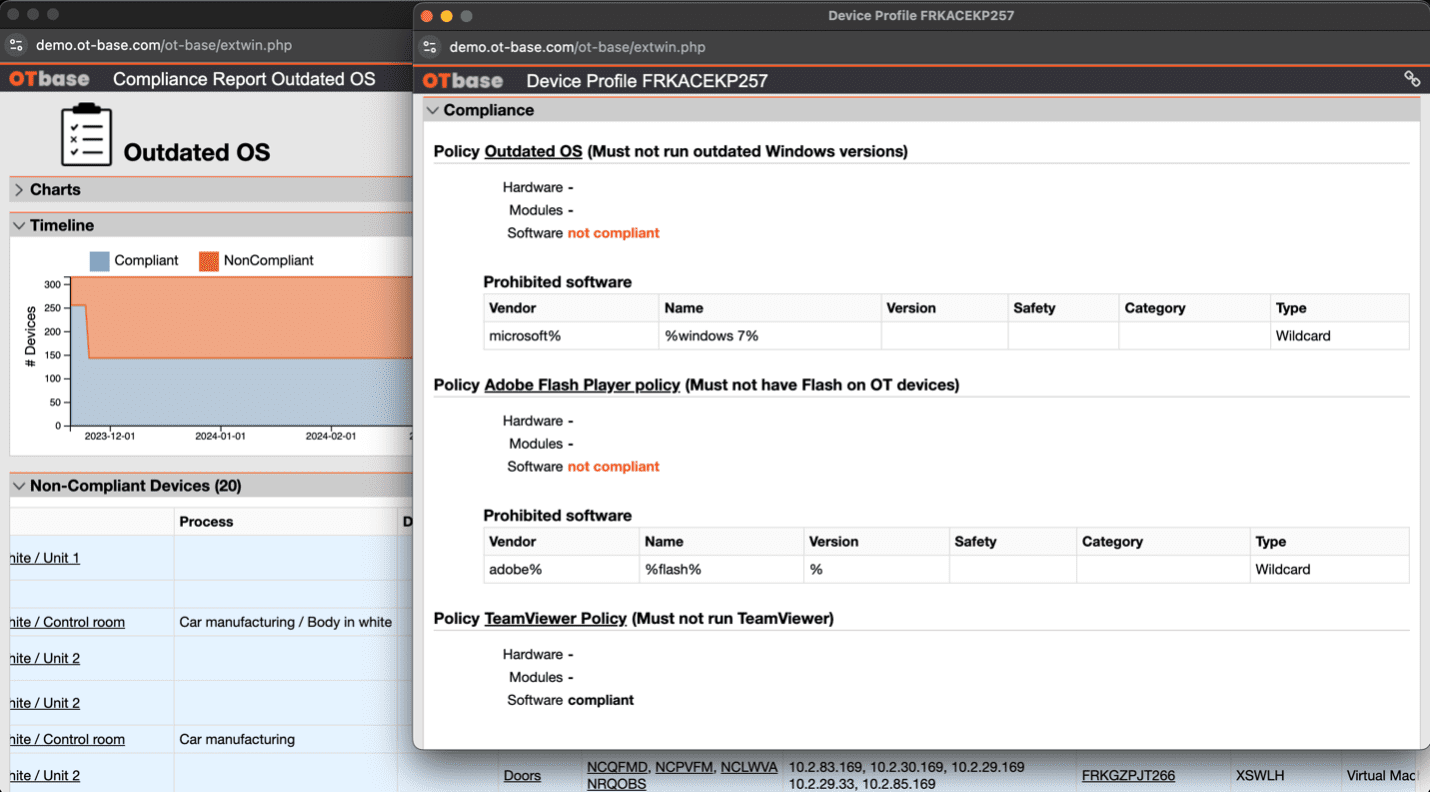
Using Automated Audits for Continuous Improvement in OT Security
Chances are, you have a real problem on your hands. More than likely, at least one Windows machine in your installed base is running Windows XP. You don’t have to…
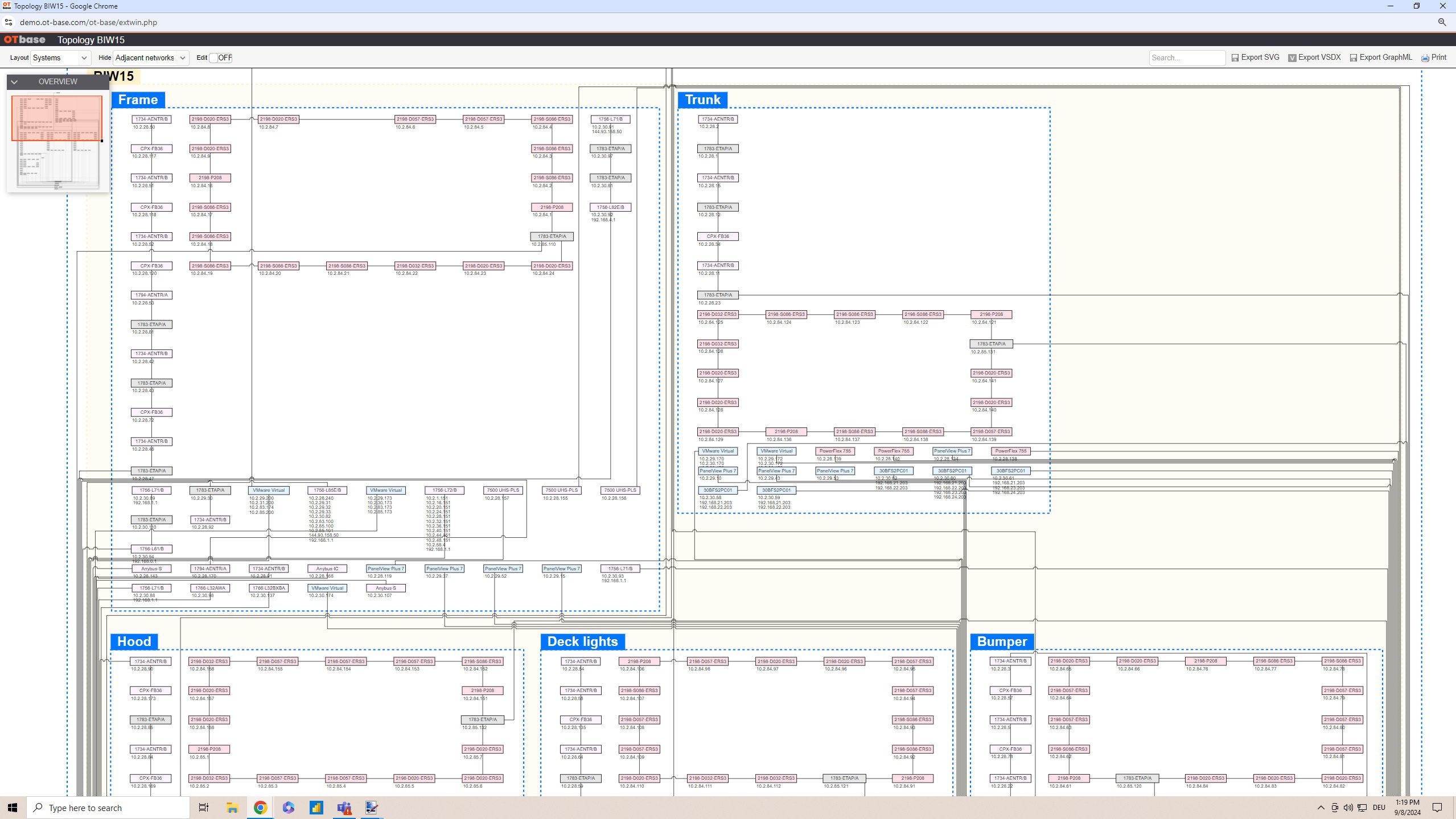
Beyond OT security basics: The role of an OT network inventory
OT environments usually stretch over hundreds of networks – each varying in criticality to whatever industrial processes they’re a part of. But it isn’t easy to converse about OT security…
